Table of Contents
NIST Cyber Security Framework
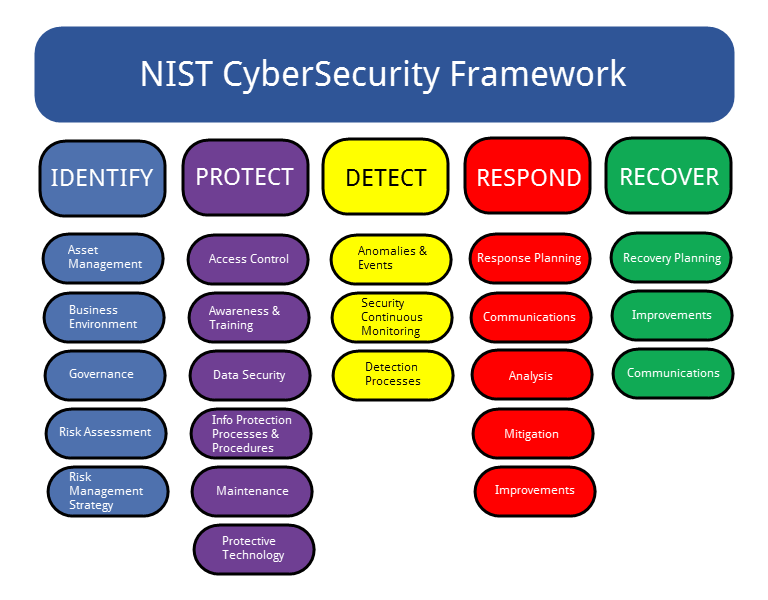 As defenders we need to wear multiple hats at all times. The NIST Cybersecurity Framework defines these hats in 5 core functions: Identify, Protect, Detect, Respond, and Recover.
As defenders we need to wear multiple hats at all times. The NIST Cybersecurity Framework defines these hats in 5 core functions: Identify, Protect, Detect, Respond, and Recover.
Here is a 4:34 min video for an overview of the NIST CSF:
If you don't like to orient yourself with the help of a framework, here are some links to other explanations of the defender's role:
Although you will never actually work in the below workflow, it makes sense from a theoretical perspective and lets us put everything into buckets 

Identify
In a Nutshell: Know what you need to protect!
To be able to protect your networks, systems, and identities, you need to know them. And while that is easy in a small business or home network, it becomes a huge task in an enterprise network. Depending on the size of the network(s) you are supposed to protect, you will need a spreadsheet, or a fully fledged asset management tool. But before we go down that path, let's talk about the why - Here are some reasons for why you need to know your assets:
- Computers are connected through networks in our days. In addition IT departments are always busy and under-resourced, so they don't secure all computers as if those would be exposed directly to the Internet. Therefore, computers on your internal networks are usually able to talk freely with each other, which allows adversary to quickly move laterally from the first compromised computer on your internal network.
- Most likely you are not responsible for the configuration and maintenance of all computers on your internal networks. Therefore, you do not know what state all the computers are in and whether they have any vulnerabilities (software bugs, weak configurations), so you can address those when you put on your Protect function hat.
- Without knowing all your assets you will not be able to implement detection mechanisms that make you aware of potential or real compromises, which will lead to unwanted surprises for the organization.
- Without knowing all your networks and assets, it will be very hard to respond to incidents and contain/eradicate threats on your networks and systems.
There are 3 disciplines in the Identify function:
- Network Management: Provides the knowledge about what networks you have and how they are connected or segmented. This knowledge is strategically important because it allows you to place network firewalls between the asset that you would like to protect and the adversary (who most often connects through the Internet).
- System/Asset Management: Provides the knowledge about all the computers you have. What are their hostnames, IP addresses, operating systems, etc.
- Vulnerability Management: Provides the knowledge about vulnerabilities that might be present on your systems/assets.
Relevant Wikipedia Articles
Protect
In a Nutshell: Minimize Attack Surface!
Protection should be applied to Networks, Systems, and Identities.
Network Protections
In the network layer of IT infrastructures the following protective technologies are available:
Relevant Wikipedia Articles
System Protections
Systems can be protected in Active and Passive ways. Active Protections include things like Anti-Virus solutions. Passive Protections are usually based on System Hardening practices. Here are some system protection techniques:
- Autonomous automated Backups (If they aren't automated it's just a snapshot, not a backup.)
Identity Protections
Identities are user accounts in your central user directory (i.e. Active Directory) or local user accounts on your systems. User accounts can be normal user accounts or privileged user accounts. Privileged user accounts should be protected better because they often have wide-reaching permissions on many systems. Within the realm of IDentity Protection there are two main topics that are worth building programs around:
Detect
In a Nutshell: Be the first to know that something malicious is happening in your environment!
There is this old quote: There are only two types of companies: The ones that have been hacked and the ones that don't know that they have been hacked. (However, now in 2021 literally everyone has been hacked.)
Detection of suspicious and malicious activity on your networks & systems and with your identities & data will give you the opportunity to do something about it before it results in huge headaches. The two biggest technology areas within detection are network security monitoring (capture network traffic and analyze it) and security log monitoring (collect all security logs and analyze them).
Network Security Monitoring
With the arrival of broad encryption of network traffic this discipline has changed dramatically in the last couple of years. Due to the applied cryptography to most network connections it becomes increasingly harder to analyze the payload of network packets. For this reason this technology field is currently changing towards analyzing the meta data of network traffic. Meta data of network traffic includes what types of connections have been made between which systems and how much data was exchanged.
Network Security Monitoring Tools
- Snort (OSS)
- Suricata (OSS)
- Security Onion (OSS + ProfSvc)
Relevant Wikipedia Pages
Security Log Monitoring
The Security Log Monitoring field splits into three disciplines - The production of Logs, the Collection of Logs, and the Analysis of Logs.
Producing Security Logs
There are many different types of security logs - Here are some examples:
- EDR Logs
- Anti-Virus Logs
- OS Security Logs
- Authentication Logs
- Firewall Logs
In most cases the default settings of the Log Sources are insufficient, so they need to be configured in some way to be useful and strike the right balance of eating up system performance and providing relevant signal to the cybersecurity team.
Collecting Security Logs
The collection of security logs is usually done with a Security Incident & Event Monitoring (SIEM) tool. SIEMs need a lot of storage for storing all the collected logs. Log Retention is what you use to define how much log data you keep around for how long, which will help you limiting costs. Most setups use a retention period between 30 days and 1y, with 90 days being the most practical.
SIEM tools
Analyzing Security Logs
Once Logs are being collected, the events within the logs need to be analyzed. Due to volume this task cannot really be done manually, technology is needed. There are two different types of Log Analyzers:
- Static Alert Rules - Create an alert when certain events or groups of events show up in the logs.
- ML model based Alert Rules - Machine Learning models detect abnormal behavior.
Static Alert Rules are traditionally a feature of SIEMs. Machine Learning models are the core function of UEBAs (User & Entity Behavior Analytics). The process adapting Alert Rules to your IT environment is called Writing Detections.
Respond
In a Nutshell: Kick em out!
Recover
In a Nutshell: Rebuild what has been brought down and learn from what happened!